We are showing you a translated content by identified your browser.
Annoying attack to my server.
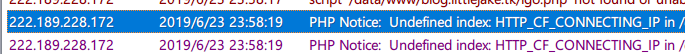
Use a honeypot to capture IP, but...
attack through the Cloudflare but without HTTP_CF_CONNECTING_IP header.
damn
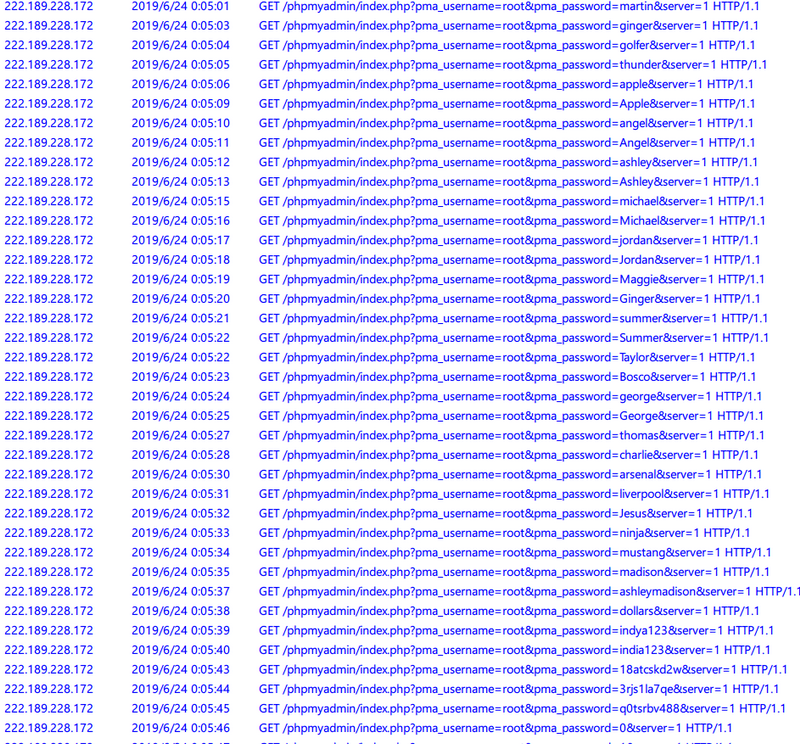
Next, brute force attack my PHPMyAdmin (mysql)
I wonder why phpmyadmin don't povide anti brute force attack.
Even a captcha.
deeper analyze
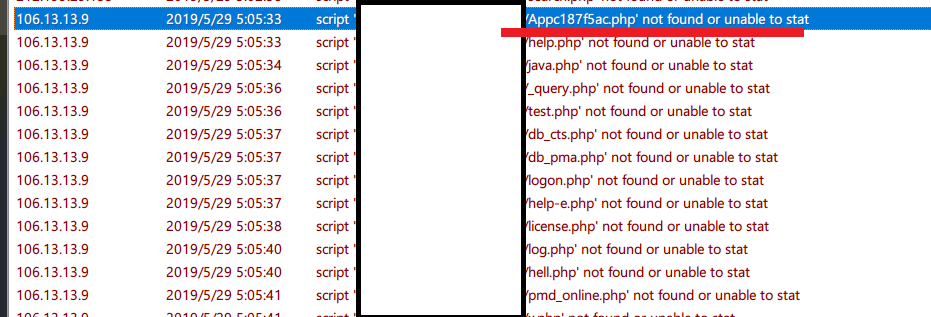
- symbol 1:It will first scan
POST /Appc187f5ac.php HTTP/1.1 - symbol 2:Massively use the same IP visit PHPMyAdmin continuously
- symbol 3:Attack lasts for 20 mins about 1QPS speed
- symbol 4:visit http but not https
Simple solution Apache version
Forbid IP according to symbol 1 and write it into hosts.deny (Linux).
- Create a shell file and copy the code below.
#!/bin/sh
WWWLOG=wwwlog directory
LIST=`cat $WWWLOG/*/access.log | grep Appc187f5ac | uniq | awk '{print $1}'|sort`
for IP in $LIST
do
grep $IP /etc/hosts.deny > /dev/null
if [ $? -gt 0 ]
then
echo "all:$IP" >> /etc/hosts.deny
fi
done
chmod +xgrant permission to the script.- using crontab to execute it per 5 mins
root $ crontab -e
*/5 * * * * sh 'script position'Massive abuse IP in my hosts.deny. Update every 5 mins
including lots of ssh brute force attack IP